sentinel
The following document outlines how external SIEM solutions, such as Microsoft Sentinel, can integrate with the Skpr hosting platform.
Credentials
The Skpr platform team will provision a role in accordance with the following Microsoft document.
Implementation
CloudTrail
Actions taken by a user, role, or an AWS service are recorded as events in CloudTrail.
The Skpr platform team have developed a logging pipeline which provides you with a filtered set of CloudTrail logs that are associated with your developer account interactions.
The diagram below outlines the flow of event logs through the system.
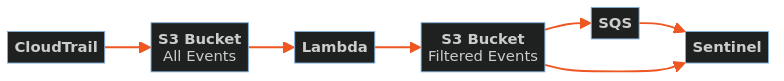
Integration Points
| Service | Format |
|---|---|
| SQS | Queue item in the format of a S3 put notification |
| S3 | CloudTrail log files stored as compressed JSON (gzip) |
CloudWatch Logs
The Skpr hosting platform stores all platform logging data in CloudWatch Logs.
The Skpr platform team can, at the request of the client, provision additional infrastructure for extracting these logs and storing them in a way which is compatible with the Microsoft Sentinel S3 connector.
Examples of logs which can be exported include:
- CloudFront
- Application
The diagram below outlines the flow of event logs through the system.
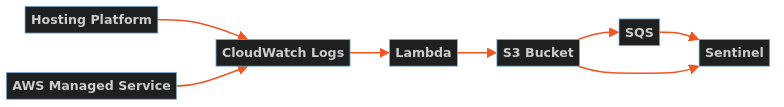
Integration Points
| Service | Format |
|---|---|
| SQS | Queue item in the format of a S3 put notification |
| S3 | Objects are stored as compressed JSON (gzip) |