System Security Plan
An overview of the Skpr System & Security.
Introduction
System Name
Skpr (https://skpr.com.au)
System Overview
The Skpr hosting platform leverages the Information Security Registered Assessors Program (IRAP) assessed Amazon Web Services (AWS) and their associated services.
System Classification
The Skpr hosting platform is designed to be able to achieve and maintain security accreditation up to PROTECTED.
System Purpose and Scope
Skpr is a cloud service provider for hosting web applications.
It is built on top of Amazon Web Services (AWS) and Kubernetes to offer a simple, cloud native solution, for hosting applications.
System Boundary
The system boundary is at the AWS account.
Below is an overview of the Skpr hosting platforms architecture.
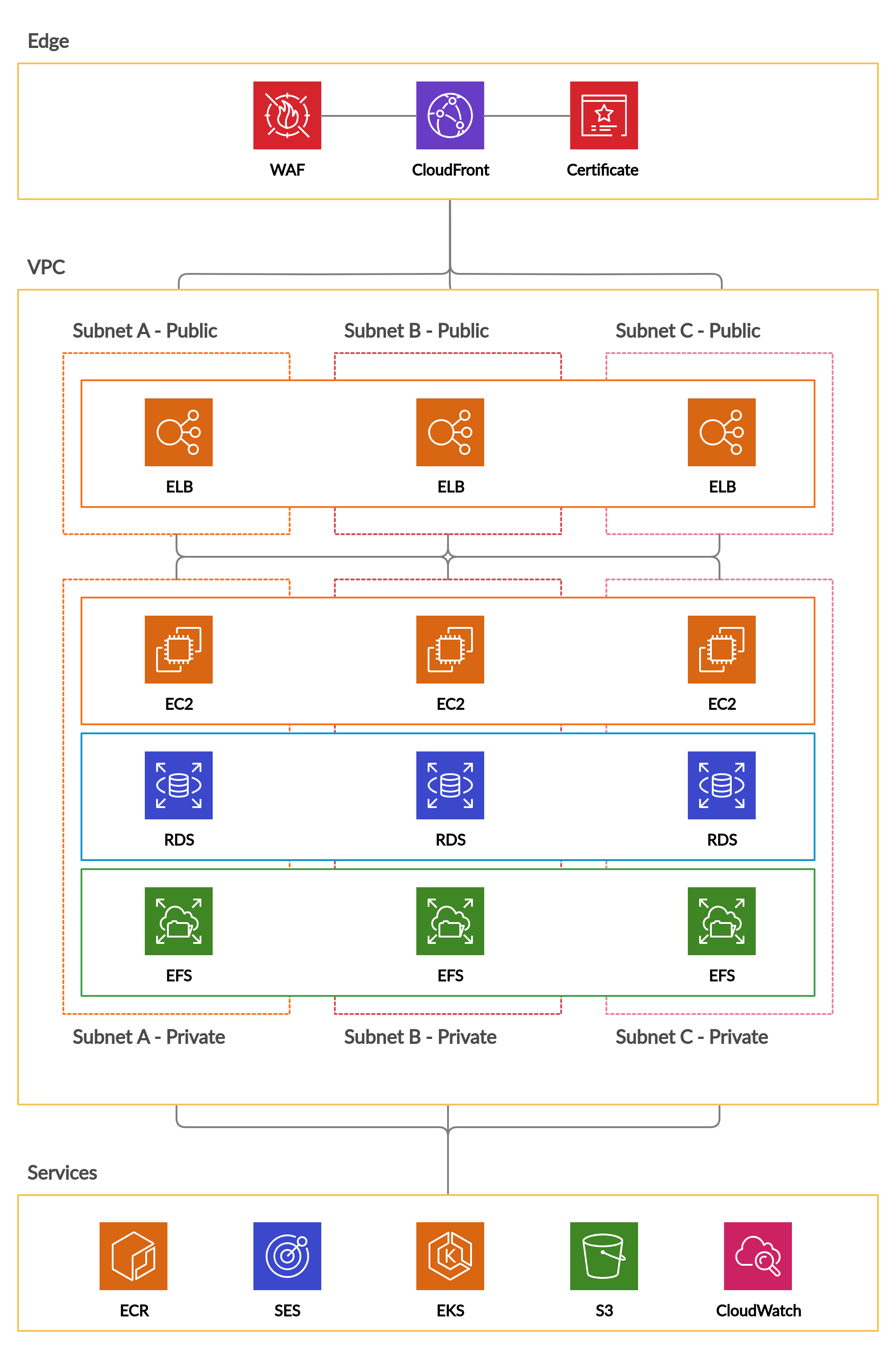
Document Purpose and Scope
The purpose of this System Security Plan (SSP) is to describe the security implementation of the Skpr hosting platform, including the underlying AWS components that are leveraged in this deployment.
Overarching security policies
The security policies that the Skpr hosting platform has been designed to comply with are listed below:
- The Australian Government ISM (March 2022) controls.
- The Australian Cyber Security Centre (ACSC) Strategies to Mitigate Cyber Security Incidents, including the Essential Eight Maturity Model.
Related security documentation
- Cyber Incident Response Plan
- Security Risk Management Plan
- AWS IRAP Assessment (https://aws.amazon.com/compliance/irap)
Risk Assessment
The results of the internal threat and risk assessment undertaken on the Skpr hosting platform are documented in the Security Risk Management Plan (SRMP).
Assessment of Services
The current security assessment status of each AWS service which the Skpr hosting platform leverages can be found below.
| Service | Assessment Status |
|---|---|
| Amazon CloudFront | Yes |
| AWS Certificate Manager | Yes |
| AWS WAF | Yes |
| AWS ALB | Yes |
| Amazon VPC | Yes |
| Amazon EKS | Yes |
| Amazon EC2 | Yes |
| Amazon EFS | Yes |
| Amazon RDS | Yes |
| Amazon CloudWatch | Yes |
| AWS Backup | Yes |
| Amazon ECR | Yes |
For more information see:
https://aws.amazon.com/compliance/services-in-scope
Cyber Security Roles
Roles available on request.
Cyber Security Incidents
Detecting Cyber Security Incidents
The Skpr hosting platform leverages the following technologies for detecting cyber events/incidents.
- Intrusion detection services configured e.g. Falco
- AWS GuardDuty configured
- Event logging and auditing configured for both AWS and Skpr API interactions
- Web Application Firewall (WAF) events
All the above sources result in an AWS CloudWatch alert to the Skpr Platform Team.
Managing Cyber Security Incidents
Management of cyber security incidents can be found in our Risk Management Plan and Cyber Incident Response Plan documentation.
Reporting cyber security incidents
Reporting of cyber security incidents can be found in our Cyber Incident Response Plan.
The Skpr hosting platform also implements client focused cyber security reporting processes where required.
Outsourcing
Cloud Services
The Skpr hosting platform is built on top of Amazon Web Services (AWS), which has been IRAP assessed by ASD (Australian Signals Directorate).
All services are provisioned within Australian data centers (ap-southeast-2 region).
AWS provides a shared responsibility model which outlines how security responsibilities are shared between itself and the Agency. Details on this shared responsibility model can be found here:
https://aws.amazon.com/compliance/shared-responsibility-model
Security Documentation
Development and Maintenance of Security Documentation
The Skpr hosting platform provides security documentation that clients can review, approve and incorporate into the broader security documentation.
All security documentation is updated as required and a “last updated” date can be seen within the history of the document in Google docs.
System-Specific Security Documentation
The Skpr hosting platform provides a suite of security documentation.
This documentation includes:
- Disaster Recovery Plan
- System Security Plan (this document)
- Cyber Incident Response Plan
- Vulnerability Management Plan
- Security Risk Management Plan
- Data Breach Response Plan
Physical Security
The Skpr platform is hosted in secure AWS data centres located in the Asia Pacific Region (Sydney). AWS utilises multi-factor authentication mechanisms for data centre access as well as additional security mechanisms designed to ensure that only authorised individuals enter an AWS data centre. Authorised employees/contractors must use their badge on the card reader and enter their unique PIN to gain access to the facility and rooms for which they are authorised. The only publicly accessible area within an AWS data centre is the lobby, and since AWS data centres are not open to the public, visitors must be admitted by a security guard stationed in the lobby.
Physical access to the data centres within the system boundary is enforced by AWS’s electronic access control system, which comprises card readers and PIN pads for building and room ingress and card readers only for building and room egress. Enforcing the use of card readers for building and room egress provides anti-pass back functionality to help ensure that unauthorised individuals do not tailgate authorised persons and get in without a badge.
Amazon’s physical security controls are fully effective and are assessed as exceeding the ISM requirements for storage of UNCLASSIFIED (DLM) data.
Additional information regarding the security and compliance of Amazon AWS:
Personnel Security
The Skpr hosting platform has a comprehensive RBAC system that ensures that development team members can only access what is required of their role.
Roles are listed on the Skpr documentation site:
https://docs.skpr.io/resources/security/rbac
All interactions/events are logged to a central logging system using AWS CloudWatch Logs.
System Hardening
The Skpr hosting platformed is hardened at multiple layers.
All applications are fronted by an AWS Web Application Firewall (WAF) instance which monitors and blocks malicious traffic. All WAF instances are configured with managed rulesets which block vulnerabilities such as the OWASP Top 10.
https://aws.amazon.com/marketplace/solutions/security/waf-managed-rules
Skpr projects benefit from a suite of Docker container images which only include the bare essentials of what is required to run the application.
All Skpr environments are deployed with a read only root filesystem. This ensures that an attacker cannot modify the application code as part of a security incident.
The Skpr hosting platform leverages upstream AWS AMI images which are specifically packaged for integrating with AWS Kubernetes Service (EKS).
The Skpr hosting solution leverages AWS Identity and Access Management (IAM) for controlling system access. Which means all platform interactions are logged and monitored.
System Management
All system administration interactions are managed using Terraform and infrastructure as code best practices.
All system changes go through a peer review process which also performs automated integration testing.
System administrators are able to access and review platform configurations via the AWS Console.
Development teams are able to review both application monitoring information via the AWS Console.
Information related to system patching is outlined in the Vulnerability Management Plan document.
Our backup management system is outlined in the Disaster Recovery section of our documentation website.
All system administration accounts are decommissioned on termination and reviewed annually.
System Monitoring
All system metrics and logging data are aggregated to AWS CloudWatch.
System administrators and development team have access to a set of pre-configured dashboards which provide an overview of the systems health.
Dashboards include:
- Web Application Firewall
- Project Environment
- MySQL
- Redis
- OpenSearch
- Filesystem
- Intruision Detection
- Kubernetes Security
Key metrics from these dashboards are also configured to trigger alarms in the Skpr platform team's incident response management software.
Email Management
All outgoing email is managed using AWS Simple Email Service (SES).
The Skpr platform team collaborates with clients to also setup DKIM for their projects.
Network Management
Skpr enables highly available, secure architectures by deploying a network solution across three availability zones and three subnets.
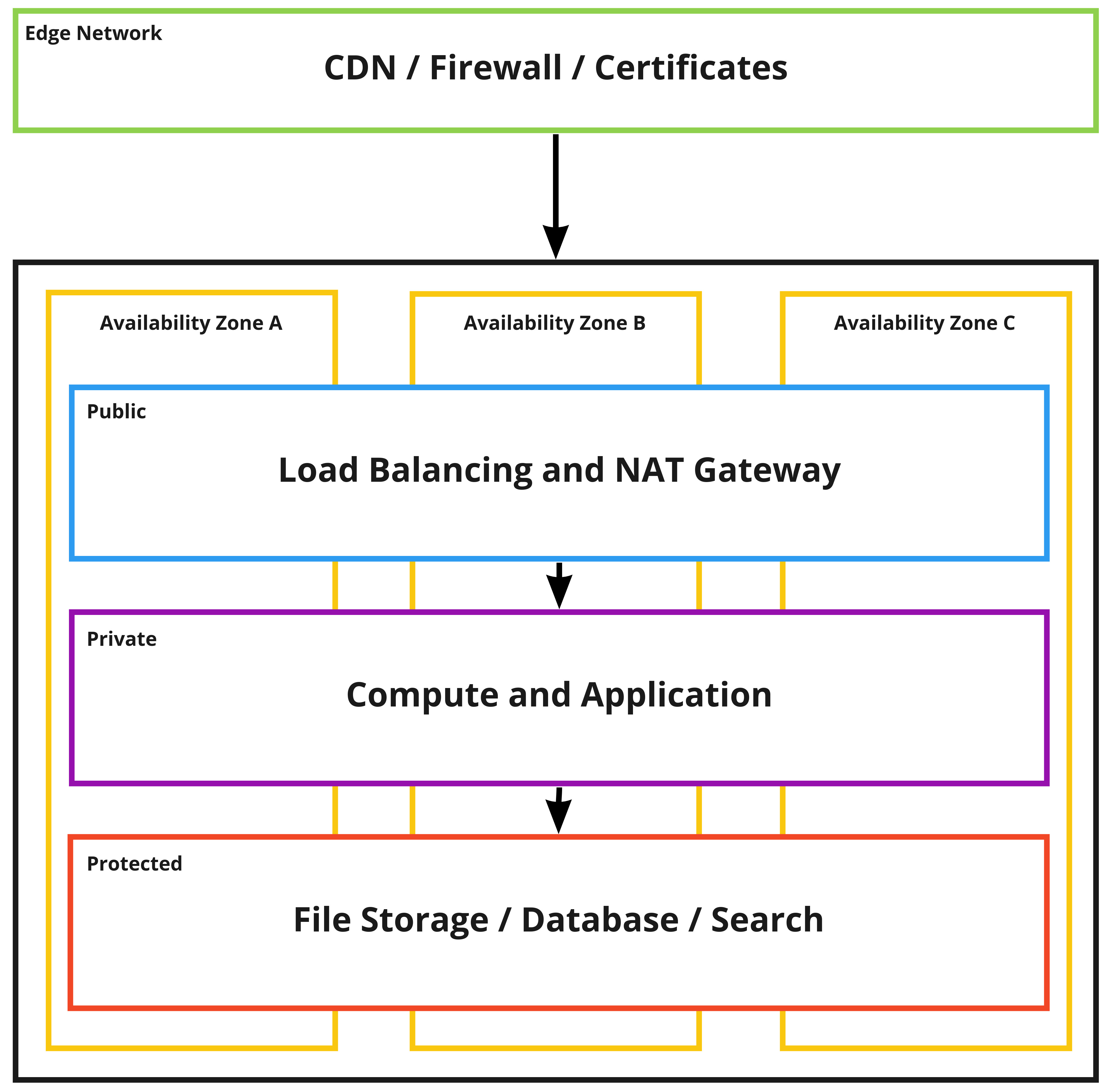
Using Cryptography
Skpr enforces HTTPS encryption for all web traffic to the Cloudfront endpoint.
CloudFront is configured by default to use the following security policy: TLSv1.2_2021.
The connections from Cloudfront to the load balancer and application to the database are also encrypted.